Category: Pen Testing
-
Trilium Notes – Self-Hosted Server Setup
I’ve been looking for a OneNote alternative for a few years now, but haven’t been able to find anything that combines the same basic functionality with a simple, clean interface. As I’m increasingly moving away from Microsoft products, I realized it was time to find a dedicated solution and stick with it. I’m excited to…
Written by
-
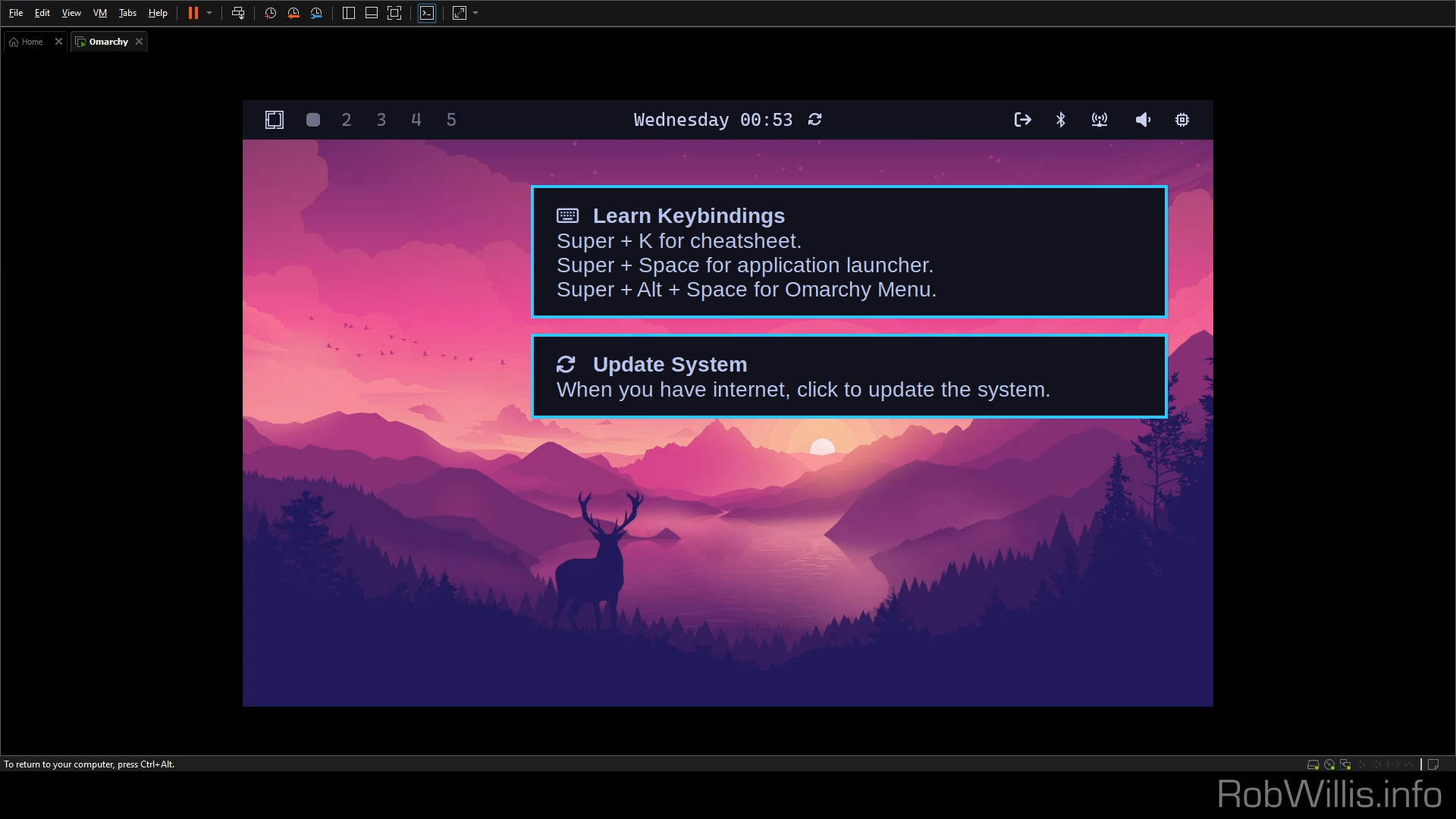
Installing Omarchy On VMware Workstation
If you’re trying to run Omarchy on VMware Workstation, you might be experiencing some issues with the GUI after what appears to be a successful installation. With the basic graphics option configured on the virtual machine, Omarchy will boot but then fall to a black screen right after entering the password. Enabling accelerated graphics gets…
Written by
-
Home Lab (2025)
It’s been a while since I’ve made a video, and even longer since I’ve shown my home lab setup! I’ve been doing some cleaning and thinking about upgrades, so I figured now would be a good time to show where everything currently stands.
Written by

-
Windows EDR: Telemetry & Sensors – Mind Map
I recently read Evading EDR by Matt Hand. While not a lengthy book, it’s technically dense and packed with tons of valuable information about Windows and EDR internals. It’s a fantastic resource, and I highly recommend it: Evading EDR by Matt Hand To help solidify my understanding of the concepts and apply them in future…
Written by

-
Ultimate Local AI Setup Guide: Ubuntu, Ollama, & Open WebUI
Intro & Background It seems safe to say that artificial intelligence (AI), particularly large language models (LLMs), are here to stay. As a cybersecurity professional, it has been pretty easy to find use cases for AI in my daily work, from general penetration testing and writing tools to forensics and reverse engineering. However, as with…
Written by

-
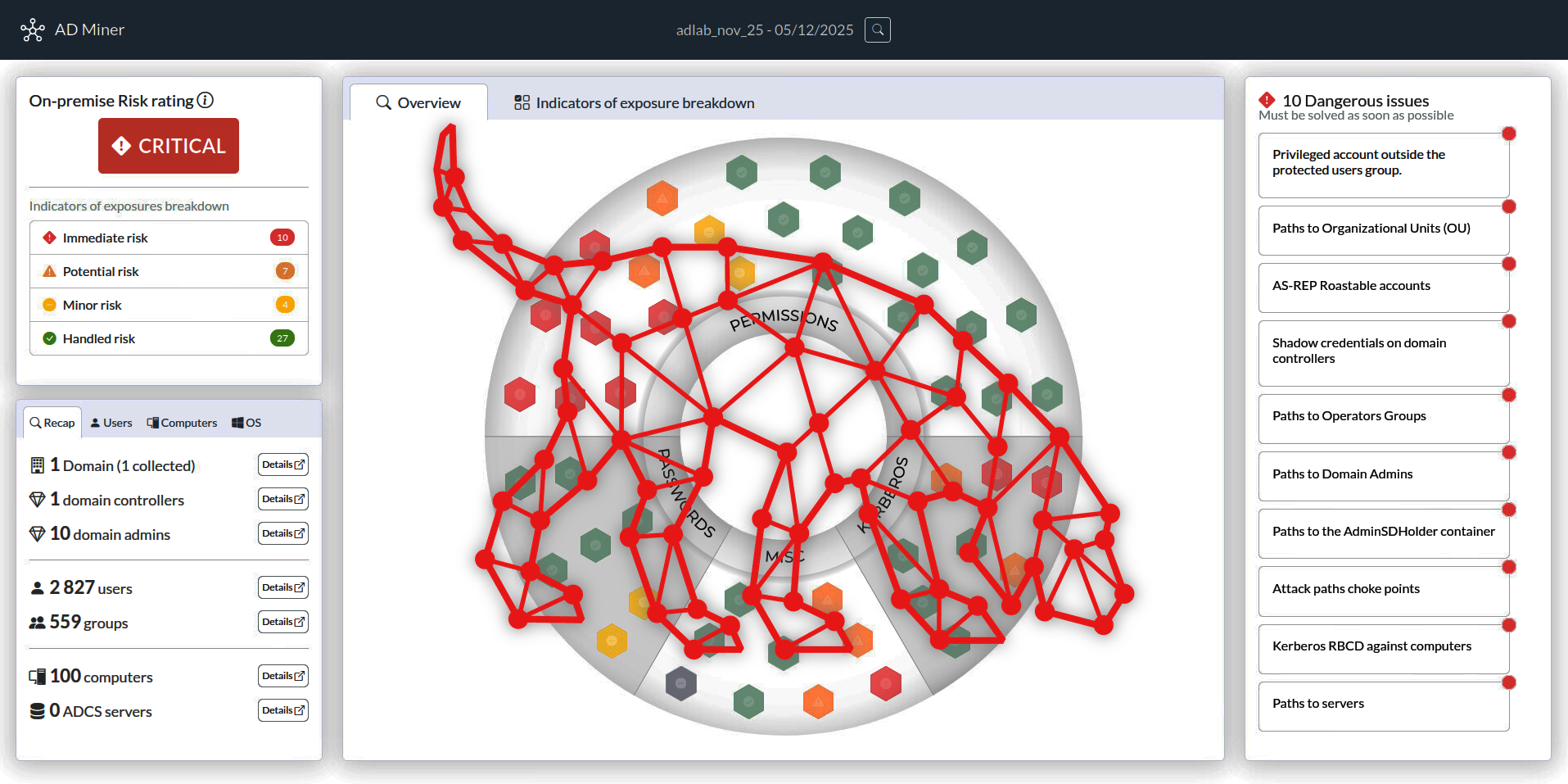
Purple Teaming AD with BloodHound CE & AD-Miner
BloodHound is one of those tools that everyone in the industry seems to have heard of and it tends to generate a buzz amongst engineers anytime it’s brought up. This reputation is well-deserved with it being such a game changer when it comes to attacking and auditing Active Directory domains. Every organization running Active Directory…
Written by

-
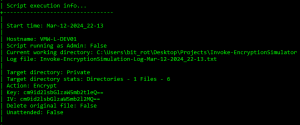
Introducing Invoke-EncryptionSimulator: A PowerShell Tool for Simulating Late-Stage Ransomware Attacks
Invoke-EncryptionSimulator Invoke-EncryptionSimulator is designed to be a simple and safe way to emulate the encryption stage of a ransomware deployment to aid in development and testing of controls focusing on file system level changes rather than process related telemetry. Invoke-EncryptionSimulator is designed to be a simple and safe way to emulate the encryption stage of…
Written by
-
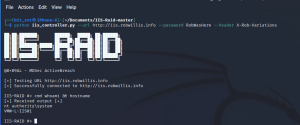
Analyzing & Detecting IIS Backdoors
IIS Extensions As Backdoors Microsoft recently published an interesting blog explaining how they’ve noticed a new trend where attackers have been leveraging Internet Information Services (IIS) extensions to covertly backdoor Windows servers: https://www.microsoft.com/security/blog/2022/07/26/malicious-iis-extensions-quietly-open-persistent-backdoors-into-servers/ The Microsoft post contains a wealth of information on this topic, but I really wanted to dig through the specifics in order…
Written by
-
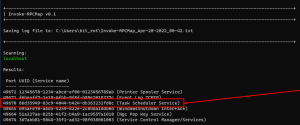
New Tool! Invoke-RPCMap: PowerShell Script for Remote RPC Service Enumeration
Invoke-RPCMap Invoke-RPCMap can be used to enumerate local and remote RPC services/ports via the RPC Endpoint Mapper service. This information can useful during an investigation where a connection to a remote port is known, but the service is running under a generic process like svchost.exe. This script will do the following: Create a local log…
Written by