If you have ever scanned your own site or a site you are responsible for you may have noticed that web servers sometimes tend to give out more information about themselves than is really needed. This information can also be used by an attacker to then target the specific versions of software the server is running by exploiting known vulnerabilities.
There are a few ways to disable some of the headers I am going to cover here, but I am only going to talk about how to use URL Rewrite to modify the headers as it is a bit more of a universal approach. This article was written around IIS 8.5 on Windows Server 2012 R2 using URL Rewrite v2.
The URL Rewrite module can be downloaded here:
http://www.iis.net/downloads/microsoft/url-rewrite
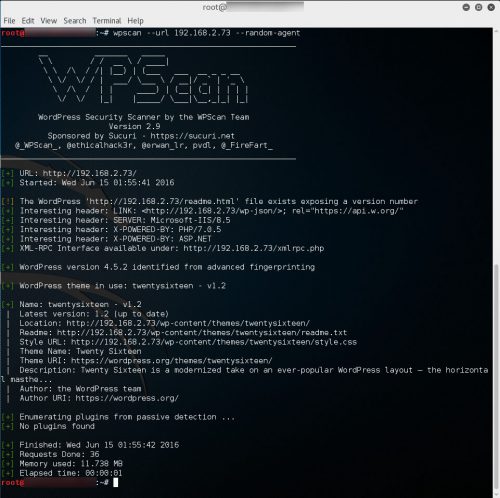
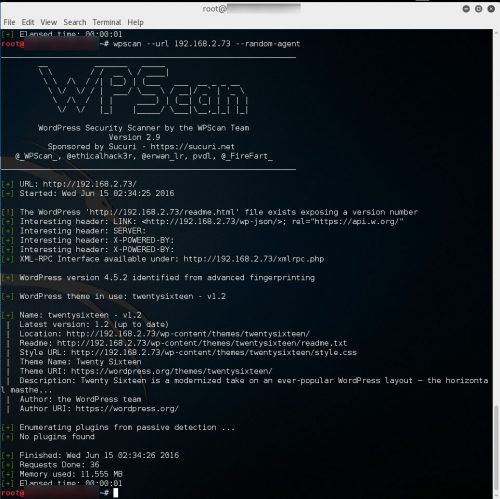
The scan results
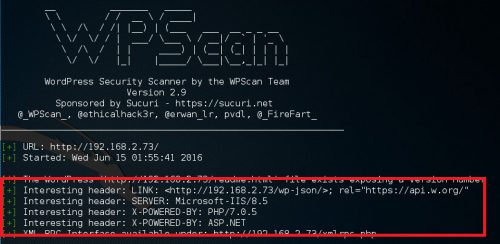
Scanning a basic WordPress site running on a Windows 2012 R2 lab vm using WPScan via a Kali Linux vm, the following “Interesting” headers returned:
I am going to focus on modifying the SERVER and the X-POWERED-BY headers.
Creating the URL Rewrite Rules
To modify the headers I am going to create outbound rules on the IIS server to rewrite the headers on the way out.
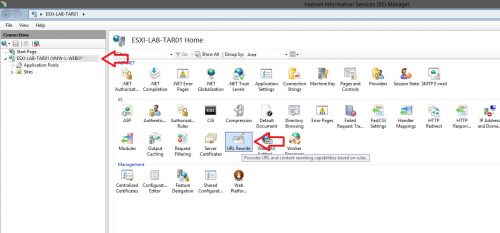
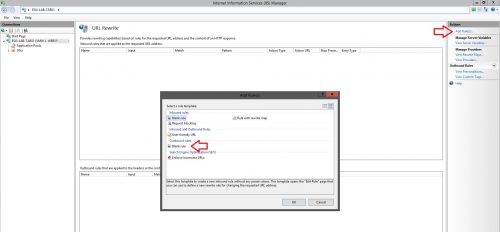
- Begin by opening IIS Manager, selecting the server level and the clicking on the URL Rewrite icon in the center pane.
- Click “Add Rule(s)…” on the right hand side and then select Outbound Rules > Blank rule and click Ok.
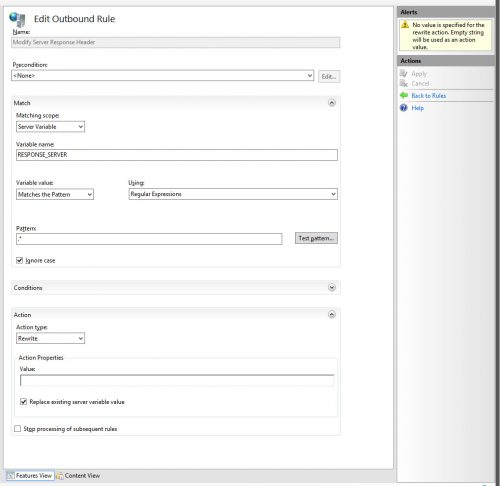
- First lets create the rule to modify the Server response and get rid of “Microsoft-IIS/8.5” by using the following settings:
Name: Modify Server Response Header
Precondition: None
Matching Scope: Server Variable
Variable Name: RESPONSE_SERVER
Variable Value: Matches the Pattern
Using: Regular Expressions
Pattern: .*
Ignore case: Checked
Action type: Rewrite
Value: (blank)
Replace existing server variable value: Checked
Stop processing of subsequent rules: Unchecked - Make sure to click Apply when complete.
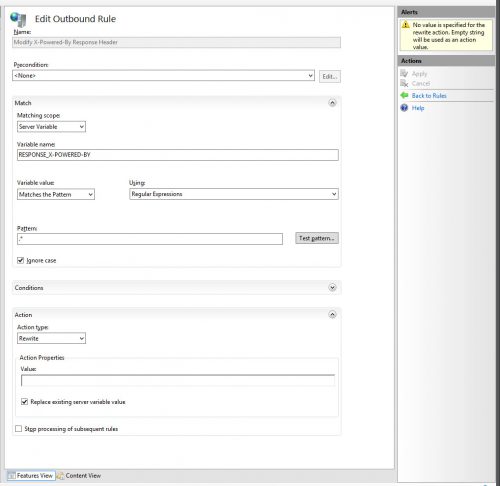
- Now to create the second outbound rule to modify the X-Powered-By responses using the following settings:
Name: Modify X-Powered-By Response Header
Precondition: None
Matching Scope: Server Variable
Variable Name: RESPONSE_X-POWERED-BY
Variable Value: Matches the Pattern
Using: Regular Expressions
Pattern: .*
Ignore case: Checked
Action type: Rewrite
Value: (blank)
Replace existing server variable value: Checked
Stop processing of subsequent rules: Unchecked - Make sure to click Apply when complete.
That’s it! Now that the rules have been created, we can test the results by rerunning the scan:
By entering a blank string in the rewrite value, the rule effectively blanks out the value returning just Server: or X-POWERED-BY: and no value. You can also put another value in there to “trick” anyone looking at this data, like setting the server to Apache when it is really running IIS.