Category: Security
-
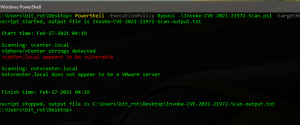
VMware vCenter CVE-2021-21972 Scanner
In this post, I am releasing a PowerShell POC script that will scan the specified target hosts and attempt to detect those that are vulnerable to VMware vCenter CVE-2021-21972. You can find the script, Invoke-CVE-2021-21972-Scan.ps1, on my github here: https://github.com/robwillisinfo/VMware_vCenter_CVE-2021-21972 The script executes in the following order: Create a log file, default log name is…
Written by
-
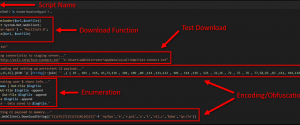
Defending Against PowerShell Attacks
It’s no secret that I am a big fan of PowerShell and recently I have been spending a considerable amount of time researching and testing it from a security perspective. While there is a lot of solid information out there, I have found it can still be a challenge to really get a solid grasp…
Written by
-
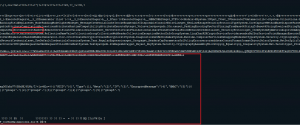
Invoke-Decoder – A PowerShell script to decode/deobfuscate malware samples
I have been spending a lot of time reviewing PowerShell based attacks and malware over the last few months and I wanted to take some time to really understand how some of the common obfuscation techniques really work under the hood. The best way for me to learn more about something like this is to…
Written by
-
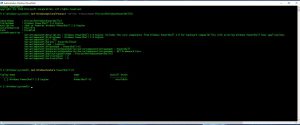
Disabling PowerShell v2 with Group Policy
In this post I am going to tackle something that I have been wanting to play around with for awhile, disabling PowerShell v2 at an enterprise scale. As a former systems engineer and now a security engineer, I have a love/hate relationship with PowerShell since it is amazingly useful but also incredibly dangerous in the…
Written by
-
Gathering Windows, PowerShell and Sysmon Events with Winlogbeat – ELK 7 – Windows Server 2016 (Part II)
In part I of this series, Installing ELK 7 (Elasticsearch, Logstash and Kibana) on Windows Server 2016, I covered the following: Installing and configuring Elasticsearch, Logstash, and Kibana as Windows services Installing and configuring Winlogbeat to forward logs from the ELK server into ELK Installing and configuring Curator as a scheduled task (optional) Now, in…
Written by
-
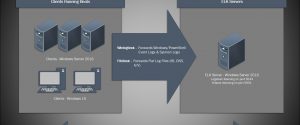
Installing ELK 7 (Elasticsearch, Logstash and Kibana) – Windows Server 2016 (Part I)
I am a huge fan of the Elastic stack as it can provide a great deal of visibility into even the largest of environments, which can help enable both engineering and security teams rapidly triage technical issues or incidents at scale. There’s also the fact that unlike Splunk, the Elastic software is free to use…
Written by
-
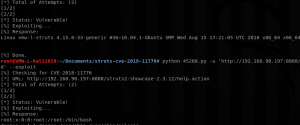
Apache Struts CVE-2018-11776 – Testing, Analyzing, & Detection
Intro Any time a new Apache Struts vulnerability comes out it should be taken pretty seriously as there are many “mission critical” systems that are leveraging the framework, with a considerable amount of them being public facing. Unfortunately, as a former Sys Ad I can tell you that many of these systems will go on…
Written by
-
My Journey Into The OSCP
Intro This post is going to break away from my typical technical how-to style posts, and talk a little bit about something that has been a personal goal of mine for some time – The Offensive Security Certified Professional. When it comes to even thinking about enrolling in the OSCP, most people will question if…
Written by

-
Home Lab Setup (2017)
In this post and video I give a quick run down of my Home Lab – everything from the rack itself, to the hardware and the basics of what everything is being used for. I started this project towards the end of 2012 with a single Dell PowerEdge 2950 GII and was hoping to teach…
Written by

