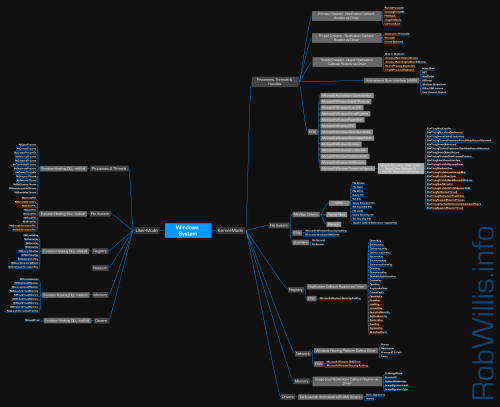
I recently read Evading EDR by Matt Hand. While not a lengthy book, it’s technically dense and packed with tons of valuable information about Windows and EDR internals. It’s a fantastic resource, and I highly recommend it:
Evading EDR by Matt Hand
To help solidify my understanding of the concepts and apply them in future projects and engagements, I wanted to take a stab at creating a mind map that highlights potential telemetry sources on Windows systems and the data they reveal. This isn’t meant to be an exhaustive list and is largely based on the information in the book, supplemented by insights from my experience as a Purple Teamer.
From a defensive standpoint, understanding the origin of the data can add valuable context. Conversely, from an offensive perspective, a technical bypass isn’t always needed. Knowing how you’re being observed can sometimes allow for effective concealment, reserve those complex bypasses for situations where they’re truly needed.